
Zobm virus description and removal. This article has been created with the main goal to get users to learn more about the recently detected Zobm virus file ransomware virus and learn how to remove it and how you can try and restore files.
The Zobm virus files, encrypted by a variant of a very dangerous ransomware strain, whose main goal is to render data on the computers it infects useless. The ransomware virus’s main goal is to get the owner of the infected computer to pay a hefty ransom fee in order to retrieve his or her encrypted files. This ransom fee is usually in BitCoin, but it may be in the form of other cryptocurrencies as well. If your computer has been infected by the Zobm virus, we recommend that you read this article thoroughly.
The Zobm Virus
Being a variant of a well-known ransomware family, which exists in relation to a lot of viruses, the Zobm virus ransomware has been reported to drop one or more executable files in the %AppData% Windows directory.
After doing so, the Zobm virus may modify the Windows registry entries, more specifically the Shell sub-key with the following location:
- HKLM/Software/Microsoft/WindowsNT/CurrentVersion/Winlogon/Shell
Then, the Zobm virus may also modify the Run registry key to run the executable file(s) in the %AppData% directory. The key is with the following path:
- HKLM/Software/Microsoft/Windows/CurrentVersion/Run/
This may result in the virus file starting automatically when you start Windows. When it starts, Zobm virus encrypts your files and then ads the .zobm file extension to every one of them. The virus also drops its _readme.txt ransom note, that looks like the following:
ATTENTION!Don’t worry, you can return all your files!All your files like photos, databases, documents and other important are encrypted with strongest encryption and unique key.The only method of recovering files is to purchase decrypt tool and unique key for you.This software will decrypt all your encrypted files.What guarantees you have?You can send one of your encrypted file from your PC and we decrypt it for free.But we can decrypt only 1 file for free. File must not contain valuable information.You can get and look video overview decrypt tool:https://we.tl/t-7YSRbcuaMaPrice of private key and decrypt software is $980.Discount 50% available if you contact us first 72 hours, that’s price for you is $490.Please note that you’ll never restore your data without payment.Check your e-mail “Spam” or “Junk” folder if you don’t get answer more than 6 hours.To get this software you need write on our e-mail:datarestorehelp@firemail.ccReserve e-mail address to contact us:datahelp@iran.iYour personal ID: ***************************************************
The developers of ransomware try to lock as many files as possible. The only data they don’t focus is usually related to the Windows processes. If they mess up the registries, .dll files or system files, your whole OS may fail to load. Such an outcome is not desired by the hackers since they will never receive any ransoms.
Unfortunately, dozens of other files may be encrypted with an AES-256 cipher, which is known to be very hard to break. If you don’t interrupt the encryption process while it is still ongoing, you should expect to lose access to all of your documents, multimedia materials, databases, projects, notes, and program-related files. The easiest way to recover the lost data is to unlock it with the original decryption key. Unfortunately, it may be easier said than done to get this tool for free.
Once the encryption finishes, the only copy of the decryption key will be automatically sent towards the Command and Control (C&C) servers of the hackers. If the computer security experts manage to breach these servers, they may extract the decryption keys database and release it for free. Unfortunate, as of now, their efforts have not been successful.
The developers of this ransomware try to deploy it to the computers of the victims via a variety of clever tactics. The hackers most commonly rely on spam email campaigns to reach unsuspecting PC users. With only a few clicks, the cybercriminals may send the infection of Zobm virus towards hundreds or even thousands of users at once. This process also involves very little operational costs and a high success rate, which explains why it is so preferred.
While the spam emails is a single tactic, it can come in very different forms. The hackers may try to look as if the malicious message was coming from banks, financial platforms like PayPal, shipping companies like DHL or famous email providers. Usually, the content of the letters mentions some unauthorized transactions or other information that may worry about the recipient. The end goal is for you to download and open the file attached to those e-mails.
The email itself contains very little information, and the supplementary data is supposed to appear in the attached file. If you make the mistake to download or open it, you may infect your machine with Zobm virus. The problem may also happen if you install programs like Adobe or Java from random suspicious platforms like the majority of adult and other software download sites.
If Zobm virus sneaks in, it will not reveal its presence immediately. It will first perform an encryption of all partitions of your hard disk. Depending on the number of files you have there, the process may take between 15-20 mins and a few hours. Zobm virus uses ‘strong’ encryption, which would be either RSA or AES. These ciphers are indeed difficult to break without the corresponding key. Unfortunately, this tool cannot be extracted from your system because it is simply not there.
As soon as the encryption ends, Zobm virus automatically transfers the key towards distant hosts, which serve as Command and Control (C&C) servers. As of now, there is no data that some security researcher has managed to breach into these databases, but it may happen in the future. Zobm virus encourages the user to pay a ransom in the form of Bitcoins, which varies from hundreds to thousands of dollars worth. The person has limited time to act – only several hours, which is a scare mechanism. The key is supposed to get destroyed when the timer reaches zero.
Zobm Removal
Zobm virus Ransomware serves as a typical file-encoding Trojan. As soon as it gets access to your machine, this crypto-malware will perform a quick scan to find the paths to all of your personal files. The targeted data includes all MS Office documents, your precious photos, and videos, your databases, the program files, etc. Only a few files such as the ones related to the core Windows processes may be spared. Once the operation ends, you will notice a threatening lockdown message on your desktop. The cybercriminals give the victims only several days to pay the ransom of Bitcoins, or else they threaten to delete the decryption key. The purpose of this frightening message is to shock the person and make him act irrationally. The victims often feel as the only solution to the issue is to pay the money. In reality, all specialists unanimously recommend not to follow the instructions of the hackers for several different reasons.
Zobm virus usually drops a ransom note file with a ransom message and places it somewhere easy to locate. It aims to ask you to pay BitCoin or other cryptos so that your files can work once more. Then, the Zobm virus may attack files with the following file types to encrypt them:
- Videos.
- Images.
- Documents.
- Audio files.
- Archives.
After Zobm virus encrypts the files, the virus leaves the files no longer able to be opened and likely appends its own file extension to them.
Zobm Virus Ransomware – How Did I Get Infected
Zobm Virus Ransomware – How Did I Get Infected
The infection process of Zobm Virus is conducted primarily via spammed e-mails that have deceptive messages embedded within them. Such messages may pretend to be sent from services such as PayPal, UPS, FedEx, and others. They may contain attachments that pretend to be invoices and other fake types of files. Other social engineering techniques include:
- Fake buttons and pictures as if the e-mails are sent from a social media site, like LinkedIn.
- Fraudulent PayPal links.
- Links to GoogleDrive and fake e-mails that look the same as if they are sent from Google.
Other infection tools may also include the usage of torrent websites and other third-party sites to upload fake updates, fake installers as well as other fraudulent executables. These executables often pretend to be:
- Software patches.
- Cracks.
- Installers.
- Portable programs.
- License activators.
- Keygens.
Zobm virus Removal
If you want to remove Zobm virus, we strongly recommend that you first backup your data, just in case something goes wrong. Then, you can follow the manual or automatic removal instructions below, depending on which type of steps suit you more. If you lack the experience and the confidence that you will remove Zobm virus manually, then you should do what most experts would and save yourself some time by downloading and running a scan with an advanced anti-malware software. Such programs are created to quickly identify and remove threats and programs with intrusive behaviours, like Zobm virus, plus they also aim to ensure that your system is protected against future intrusions as well.
The main reasons not to pay the ransom are two. First, you may not receive the promised unlocking key even after doing exactly as the hackers demand. They often scam the victims because the Bitcoin platform doesn’t allow refunds and the people have no way to get their money back. The second reason not to finance cybercriminals is that your money will only motivate them to create more aggressive ransomware like Zobm virus. On the other hand, if their attacks are in vain, they may stop spamming the web with such malicious Trojans. These parasites require quite some efforts to be created professionally and spread efficiently.
Once you decide not to pay the ransom, there are several other ways that may help you decrypt your personal files. You should begin the attempts by removing all traces of the malware. If you fail to delete Zobm virus Ransomware properly, it may decrypt your files once again in the future or spread to other connected devices. The manual removal is not the recommended solution since it requires expert-level knowledge in computers. The most reliable tactic is to use dedicated security software that has added Zobm virus Ransomware to its database. Once the scan finishes, you should try some of the programs for the restoration of files or the integrated System Restore feature. If you are lucky enough to have a spare copy of your files on some external device, you can import them back to your computer safely.
Preparation before removal of Zobm virus:
1. Make sure to backup your files.
2. Make sure to have this instructions page always open so that you can follow the steps.
3. Be patient as the removal may take some time.
Step 1: Reboot your computer in Safe Mode:
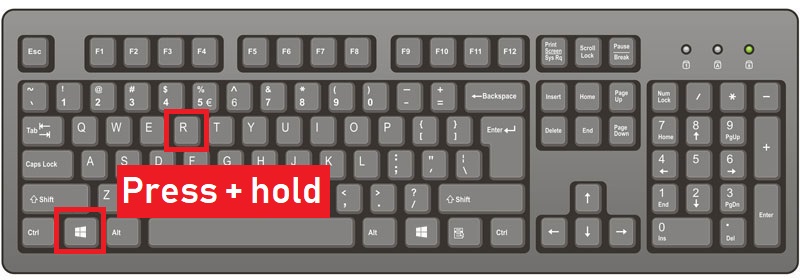
1) Hold Windows Key and R
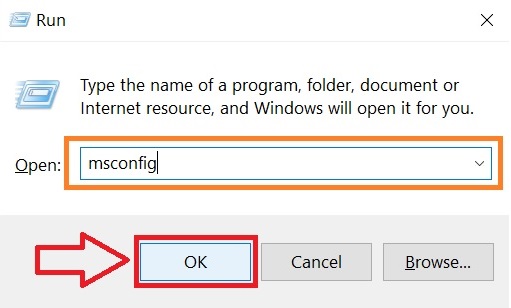
2) A run Window will appear, in it type “msconfig” and hit Enter
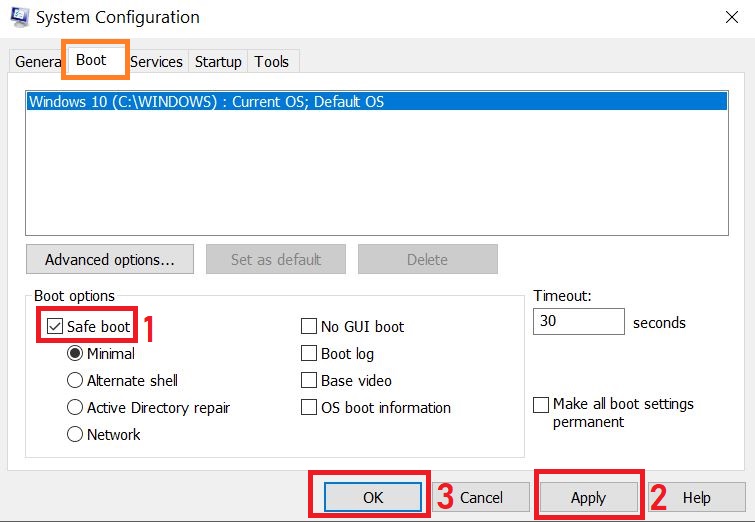
3) After the Window appears to go to the Boot tab and select Safe Boot
Step 2: Cut out Zobm virus in Task Manager

1) Press CTRL+ESC+SHIFT at the same time.
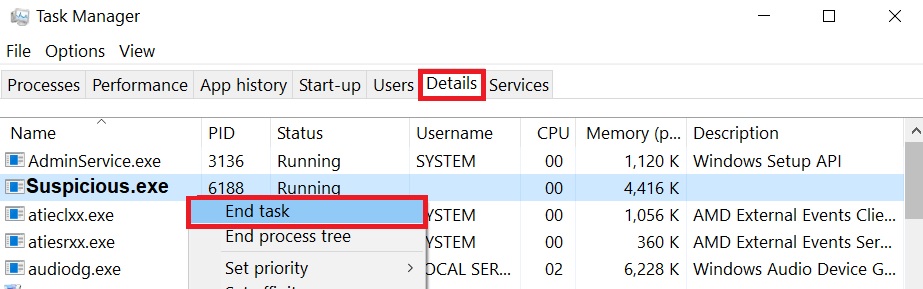
2)Locate the “Details” tab and find a malicious process of Zobm virus. Right-click on it and click on “End Process”.
Step 3: Eliminate Zobm virus‘s Malicious Registries.
For most Windows variants:
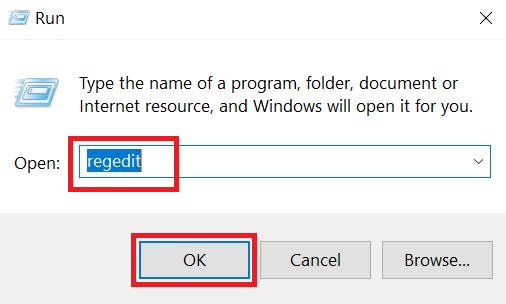
1) Hold Windows Button and R. In the “Run” box type “regedit” and hit “Enter”.
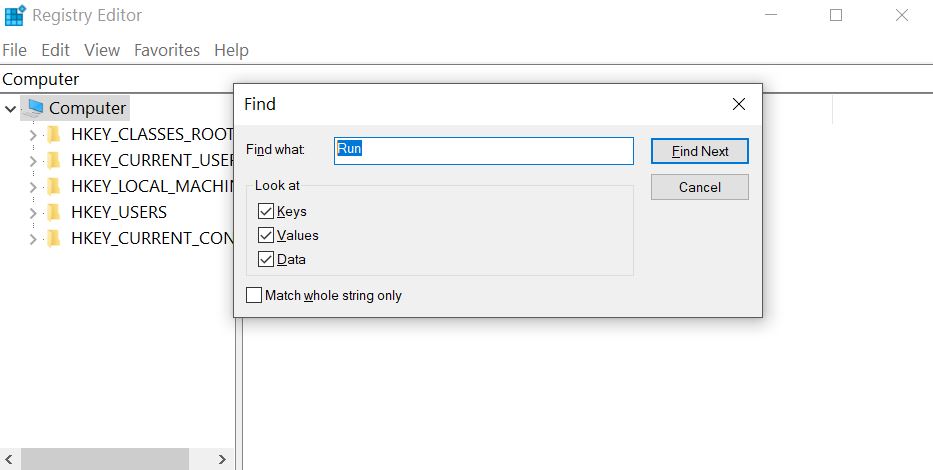
2) Hold CTRL+F keys and type Zobm virus or the file name of the malicious executable of the virus which is usually located in %AppData%, %Temp%, %Local%, %Roaming% or %SystemDrive%. Usually, most viruses tend to set entries with random names in the “Run” and “RunOnce” sub-keys.
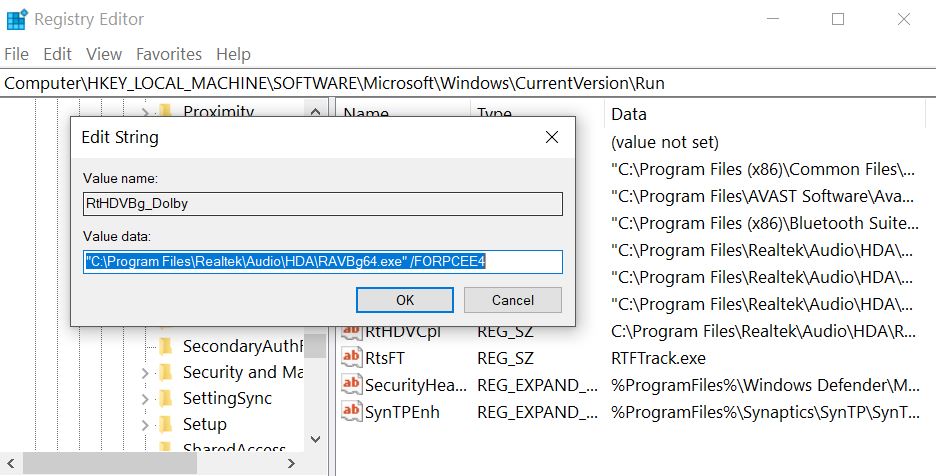
3) You can also find the virus’s malicious files by right-clicking on the value and seeing it’s data. After having located malicious registry objects, some of which are usually in the Run and RunOnce subkeys delete them permanently and restart your computer. Here is how to find and delete keys for different versions.
Step 4: Scan for and remove all virus files, related to Zobm virus and secure your system.
If you are in Safe Mode, boot back into normal mode and follow the steps below
1)Click on the button to download SpyHunter’s installer.
It is advisable to run a free scan before committing to the full version. You should make sure that the malware is detected by SpyHunter first.
The free version of SpyHunter will only scan your computer to detect any possible threats. To remove them permanently from your computer, purchase its full version. Spy Hunter malware removal tool additional information/SpyHunter Uninstall Instructions
Step 5:Recover files encrypted by the Zobm virus Ransomware.
Method 1: Using Shadow Explorer. In case you have enabled File history on your Windows Machine one thing you can do is to use Shadow Explorer to get your files back. Unfortunately, some ransomware viruses may delete those shadow volume copies with an administrative command to prevent you from doing just that.
Method 2: If you try to decrypt your files using third-party decryption tools. There are many antivirus providers who have decrypted multiple ransomware viruses in the last couple of years and posted decryptors for them. Chances are if your ransomware virus uses the same encryption code used by a decryptable virus, you may get the files back. However, this is also not a guarantee, so you might want to try this method with copies of the original encrypted files, because if a third-party program tampers with their encrypted structure, they may be damaged permanently. Most of the currently available decryptors for ransomware viruses can be seen if you visit the NoMoreRansom project – a project that is the result of combined efforts of researchers worldwide to create decryption software for all ransomware viruses.
Method 3: Using Data Recovery tools. This method is suggested by multiple experts in the field. It can be used to scan your hard drive’s sectors and hence scramble the encrypted files anew as if they were deleted. Most ransomware viruses usually delete a file and create an encrypted copy to prevent such programs for restoring the files, but not all are this sophisticated. So you may have a chance of restoring some of your files with this method. Here are several data recovery programs that you can try and restore at least some of your files.
If at the end of this, your problem is not yet still solved, kindly look at another solution below.
Drop your comments below 👇👇👇👇👇
Reference: CFOC








0 comments:
Post a Comment